Secure Shell supports various authentication mechanisms. The two most used methods are:
- Password based authentication
- Public SSH key authentication
In this article, we will discuss how to use Public SSH key authentication, which enables you to log in to your SSH server using a cryptographic key rather than a password.
Benefits of using public key authentication
- Protect against brute-force attacks
- Quick and easy to log in compared to password method
- Allow multiple users to log in without sharing single password
- Revoke a single user without affecting others
Setup public key based authentication
This tutorial covers how to setup public key based authentication on Unix-based client machine. We’ll discuss how to do this on Windows in future articles.
You need to generate a unique key pair which consists of a public key (on the server) and a private key (on the client) for each client machine.
Generating SSH key pair is done on the client machine, and then the public key is transferred to the remote server machine. However, it is possible to create the keys on the server and transfer them to the client machine. But this method is highly not recommended.
Also keep in mind that we are going to assume the server is running Linux-based OS, as most of the servers are running Linux nowadays.
The following steps will guide you through the process of configuring public key based authentication:
1- Check if you have existing SSH keys
Before generating new SSH key pair, you have to check if there is an existing key pair on your machine in the default location, otherwise they will be overwritten.
To check if existing key are present, run the following command:
$ ls -al ~/.ssh/id_*
If you see No such file or directory it means you don’t have an SSH key.
Otherwise, if it happened to be that you have a previous SSH keys that you need, you have to create a backup as we will discuss in the next step or you may skip if backup is of no concern.
2- Backup preexisting SSH keys
If there are old SSH keys in the default location and you planed to use them in the future, you have to back them up and keep them in a safe place before generating new one, as there is no way to retrieve lost private keys. But on the other hand public keys can be regenerated form corresponding private keys as we will talk about this at the end of this article.
To backup your old SSH keys use the following command:
$ mkdir key_backup $ cp id_rsa* key_backup
3- Generate new SSH key pair
To generate a new SSH key pair, use the command:
$ ssh-keygen -t rsa -b 4096 -C "any_comment_you_like"
-t specifies the type of key to be generated. -b specifies the number of bits in the key. -C to add a comment to the key.
After hitting Enter, it will prompt you to choose the location and name of the file to store the keys. The default location is preferred. However, you may need to change it according to your needs especially if you have not backed up keys already in the location and you don’t want to lose them. Press Enter to choose the default location.
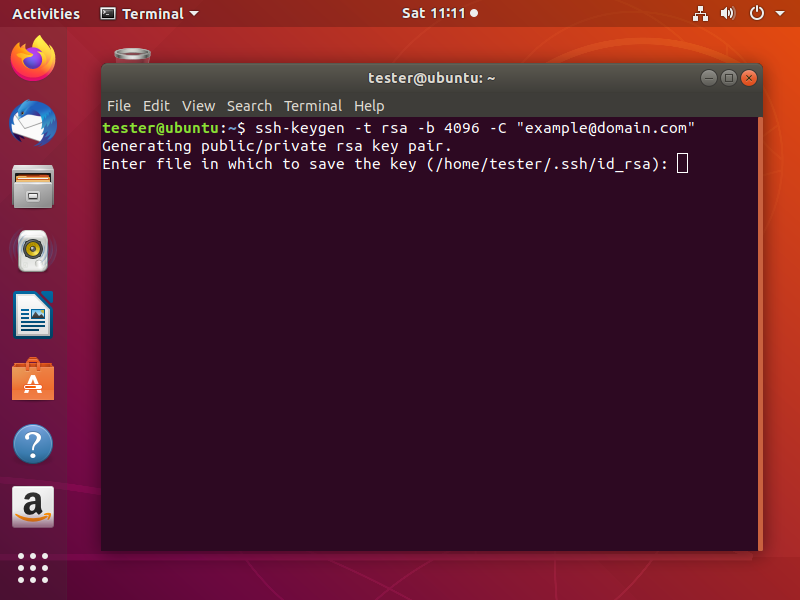
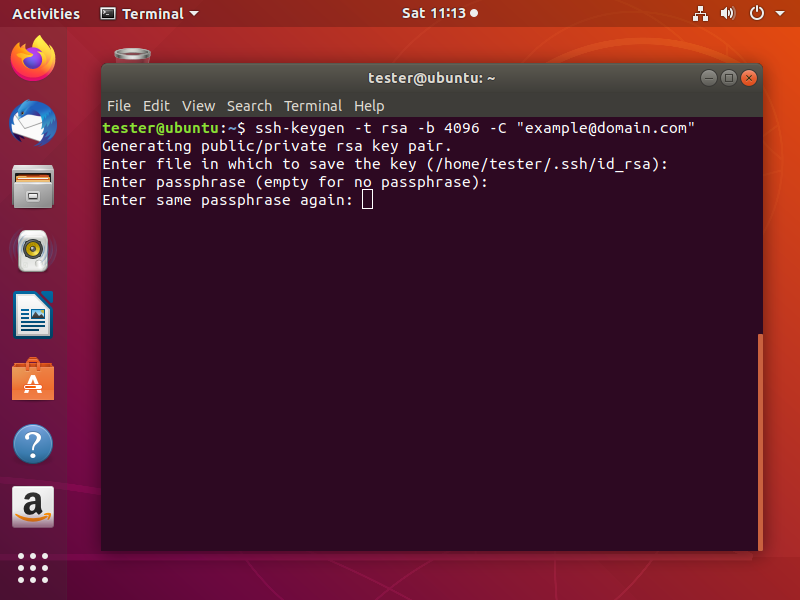
Next, you will be asked to type a passphrase. Using a passphrase means a password will be required to use the private key and it adds an extra layer of security. The most common practice is that private keys are generated without passphrase because this will be useful for automated processes. So, if you don’t want to add a passphrase just press Enter after leaving the prompt empty. Then do the same when it asks for passphrase confirmation.
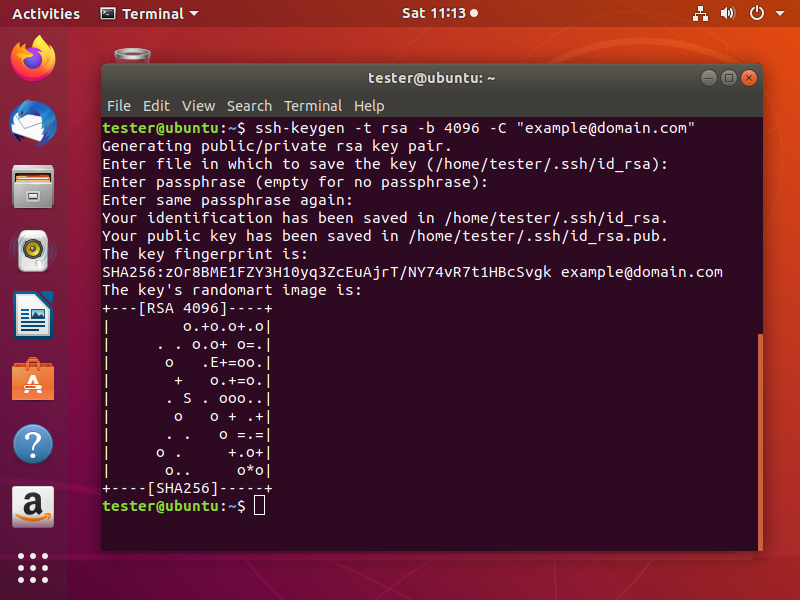
Now, your SSH key pair will be generated and a visual fingerprint will be drawn on the screen.
4- Copy the public key
After that you successfully generated an SSH key pair. Your next step is to configure the server so you can log in using the SSH key authentication.
The best method to copy your public key to the server is to use ssh-copy-id utility. On the client machine terminal run the following command:
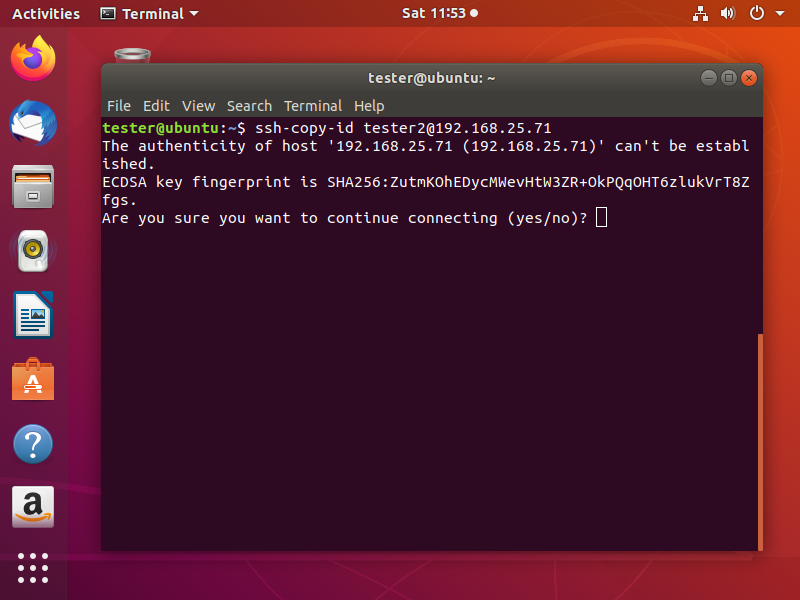
$ ssh-copy-id username@server_ip_address
If you are not connected previously to this server using this machine. Consequently, it will ask if you want to continue as the authenticity of the server is not established. Type yes and hit Enter.
Then you need to enter the password of the server. Once you are authenticated, the public key will be transferred and appended to the server’s authorized_keys file and the connection will be terminated.
There are alternative methods if ssh-copy-id utility is not available on the client machine. For instance, you can log in to the server and manually create .ssh/authorized_keys file. Then edit it using your preferred editor and paste your public key into the file. And this can be done using the following compound command:
$ cat ~/.ssh/id_rsa.pub | ssh username@server_ip_address "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"
Log in to the server using SSH keys
After you completed all the steps above you can now log in to the remote server securely without being asked to enter a password.
To log in to the server use:
$ ssh username@server_ip_address
If you want to log in using a private key that is not located in the default location, you need to specify the location using this command:
$ ssh -i /path_to_private_key_file username@server_ip_address
Configure the server for multiple keys access
The format of .ssh/authorized_keys file allows multiple keys to be appended by putting each key in a separate line.
In case you have multiple clients, each client needs to generate its own SSH key pair, and public key of each client needs to be copied to the server using the steps described above.
Using ssh-copy-id utility will automatically append new keys even if there are already previously appended keys to .ssh/authorized_keys file. Or by manually editing the file and pasting each key in new line.
Disabling password authentication
Disabling password based authentication adds an extra layer of security by preventing brute-force attacks.
Essentially, you should make sure that you can log in to the server using SSH key authentication and the user you are logging in with has sudo privileges before disabling password authentication.
In order to disable SSH password authentication you can follow these steps:
- Log in to your remote server using SSH key as root or as a user with sudo privileges
- Open SSH configuration file /etc/ssh/sshd_config
- Search for the following directives inside the file and modiy them as follows:
PasswordAuthentication no
ChallengeResponseAuthentication no
UsePAM no
- Save the file
- Restart the SSH service
To restart SSH service on Debian or Ubuntu servers, use the following command:
$ sudo systemctl restart ssh
On CentOS or Fedora servers, run this command:
$ sudo systemctl restart sshd
Retrieve public key from private key
It is possible for you to regenerate the public key form the private key. But you cannot do the reverse.
To do that, use the following command:
ssh-keygen -y -f /path_to_private_key_file
At the end, I like to mention that if you need a cloud hosting service to host your servers, I highly recommend Vultr. If you like to try it sign up using this link and get 100$ free credit for the first month to try Vultr. Try it out, there is nothing to lose. If you want to learn how to create your own server on Vultr, check out this article to learn how.
If you have any question, leave it in the comments below.
Share
Other articles you may find interesting
Advertisment


Pingback: How to transfer files remotely via SSH – ServerKernel